Introduction to OpenBSD
xhr
xhr@giessen.ccc.de • @_xhr_@mastodon.social
WTF Comic Sans?
Never heard of OpenBSD?
How about ... OpenSSH, LibreSSL, PF packet filter, OpenBGPD, tmux, mandoc?
OpenBSD's self-conception
"OpenBSD believes in strong security. Our aspiration is to be number one in the industry for security"
"Only two remote holes in the default install, in a heck of a long time!"
OpenBSD's Versions
base + ports + xenocara
Traditionally, BSDs' base system contains the Kernel and userland.
What's in a full base Installation?
Kernel, userland, OpenSSH, OpenNTPD, httpd, OpenSMTPD, OpenBGPD, LibreSSL, OpenRSYNC, relayd, NSD, unbound, VMM, tmux, compiler, Perl, X11, cwm, ...
-release
Released every 6 month
-stable
-release branch including security and errata fixes
-current
Development branch. Will be tagged as release every 6 month
Keeping OpenBSD up-to-date
Using Binary Patches
Provided via syspatch(8). For the latest two releases on amd64, arm64 and i386.
Use the source Luke!
All other architectures. Check out the -stable source and compile according to release(8).
Keeping -current up to date
Use the regularly binary snapshots. Upgrades can be done manually or fully automatically.
Packages & Ports
Packages?
Pre-built binary packages for 3rd-party applications.
Packages for -stable
Pre-built for -release. Third-Party updates via openup from M:Tier
Packages for -current
Continuously built for all architectures.
Ports
Create packages by compiling 3rd-party software from source
"In general, you are advised to use packages over building an application from ports."
Notable Differences
Default Shell
... is not bash. It's an active maintained and audited version of ksh (PD Korn Shell).
sudo anyone?
sudo is written and maintained by an active OpenBSD developer, Todd C. Miller.
sudo is dead. Long live doas
Small simple replacement for sudo with a simpler configuration grammar.
sudo vs doas
8 916 vs 515 LoC in total*
* Counted C sources and header files with cloc
Example doas.conf
permit persist user as root
permit nopass root as root
permit nopass user as root cmd /sbin/halt
permit nopass setenv { DISPLAY } user as firefox cmd /usr/local/bin/firefox
permit nopass setenv { DISPLAY } user as torbrowser cmd /usr/local/bin/tor-browser
signify
Creates and verifies cryptographic signatures. Used for signing distribution sets and packages.
But everybody else uses GnuPG!
"We wanted to ensure all the code involved in signing met our quality standards.
The complexity of the code is also a factor. All those complex features require lots of complex code, which [...] makes auditing nearly impossible. Even if a perfect PGP codebase existed, how would we be able to identify it?"
GnuPG vs signify
231 732 vs 2 100 LoC in total*
* Counted C sources and header files with cloc
One config to rule them all
Users are advised to run the GENERIC kernel configuration.
OpenBSD 6.5-current (GENERIC.MP) #50: Wed May 29 13:01:19 MDT 2019
deraadt@amd64.openbsd.org:/usr/src/sys/arch/amd64/compile/GENERIC.MP
Security Features
OK?


OK!



Extensive testing and four-eye principle
Secure by default
Have less knobs to turn and provide sensible defaults.
Exploit Mitigations
ASLR, W^X, KARL, RETGUARD, arc4random, Otto's malloc, RELRO, PIE, fork+exec, library relinking, trapsleds, guard pages, ROP gadget reduction, privsep, privdrop, ...
See Theo's presentation for more details
Clear habit towards Legacy
R.I.P.
Bluetooth support, Loadable Kernel Modules, Linux compatibility layer, /proc file system, Kerberos, several architectures, tmpfs disabled by default.
pledge(2)
General Idea
Programs use system calls to function → Take away the syscalls the program won't need to call.
Is this new?
No. It is implemented in: NSA's SELinux, FreeBSD's capsicum, Linux's seccomp (and maybe others ...).
So, why another syscall filter?
Ask yourself! How many programs you use on a daily base use them?
How is pledge(2) different?
Similar syscalls are grouped in subsets of the POSIX environment. Using syscalls outside these groups leads to program termination.
Example Subsets
| Pledge | Selected Syscalls | Remark (see pledge(2) for all syscalls) |
|---|---|---|
| stdio | close, dup, fstat, getpid, pipe, select, read, write, ... | Standard IO syscalls |
| rpath | chdir, getcwd, lstat, chmod, chflags, chown, fstat, ... | A number of syscalls are allowed if they only cause read-only effects on the filesystem |
| wpath | chdir, getcwd, lstat, chmod, chflags, chown, fstat, ... | A number of syscalls are allowed and may cause write-effects on the filesystem |
| inet | socket, listen, bind, connect, accept, setsockopt, ... | The following syscalls are allowed to operate in the AF_INET and AF_INET6 domains |
| dns | sendto, recvfrom, socket, connect | Subsequent to a successful open(2) of /etc/resolv.conf, a few syscalls become able to allow DNS network transactions |
| settime | settimeofday, adjtime, adjfreq | Allows the setting of system time |
Pledging a existing Program
Read and understand the source code. Figure out what syscalls will be used when. Pledge that only these will be used.
Different code path can have different pledges. Dropped promises cannot be regained.
Example: Pledging i3wm
Pledge in Base and Ports
Over 350 programs in base and around 50 ports:
bind, chromium, firefox, {p7,b,un}zip, i3, iridium, isync, mupdf, (neo)mutt, memcached, suricata, spectrewm, xz, ...
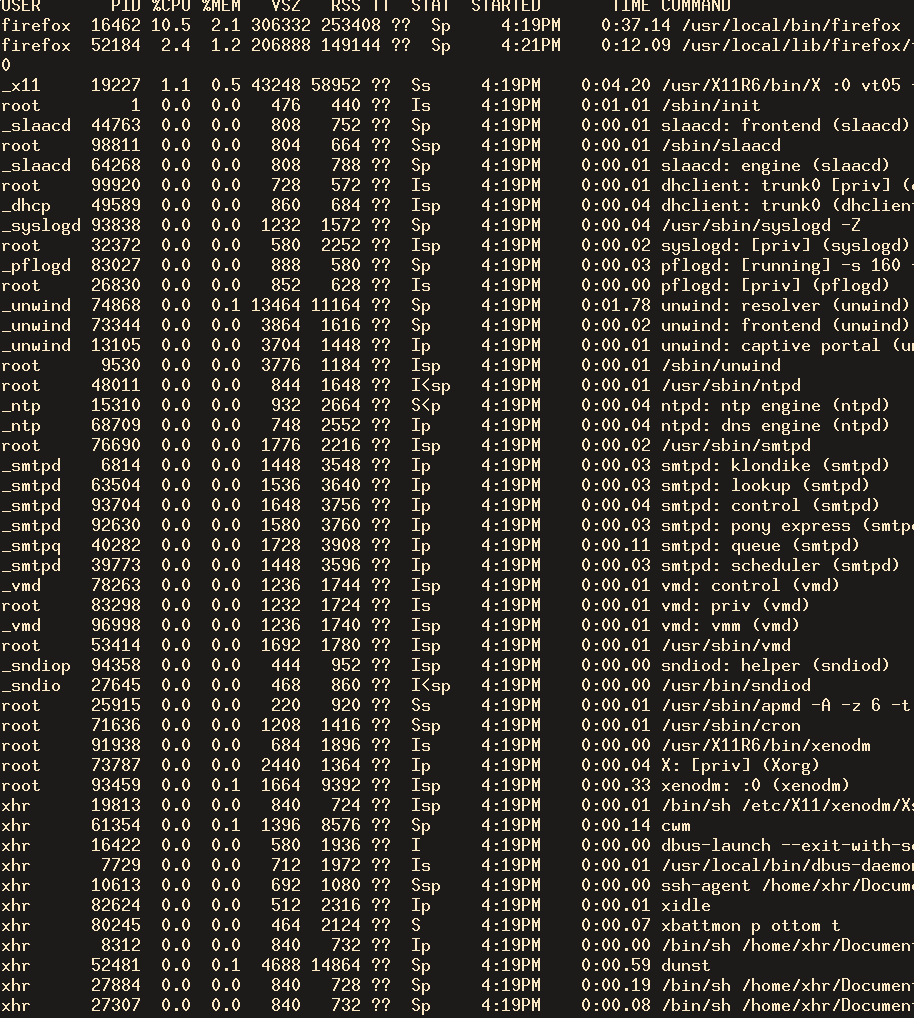
Pledge in Action
Unveil the File System
General Idea
Limit program's access to files/directories absolutely necessary to function.
unveil(path, flags); // with flags r(ead), w(rite), x(execute), c(reate)
Consequences for the Process
Access to non-unveiled path returns does not exist. Access to unveiled path with wrong flags returns access denied.
unveil Example
By default, a process sees the following
unveil("/etc", "r");
Allow read-only access to /etc only
unveil("/sbin", "r");
Further allow read-only access to /sbin
unveil(NULL, NULL);
Further unveil calls are not permitted
Unveiled base programs
acme-client, acpidump, audioctl, biff, calendar, comsat, ctfconv, dev_mkdb, doas, encrypt, fingerd, from, fsck, fsck_ffs, fsck_msdos, getconf, getent, getty, htpasswd, ifconfig, ifstated, kdump, kvm_mkdb, last, lockspool, look, makefs, mesg, mixerctl, nc, nologin, ntpd, ospf6d, ospfd, passwd, pflogd, ps, pstat, rarpd, rebound, ripd, rsync, savecore, sdiff, sensorsd, shutdown, sndiod, snmpd, spamd, spamlogd, su, syslogd, tcpbench, tcpdrop, tcpdump, tty, unbound, unwind, users, vipw, vmctl, wall, who
Hint: Its 63 :)
Unveiled Ports
Chromium. Yes, the 5M lines of code web browser.
Iridium, desktop-file-utils, shared-mime-info. So yes, there is a lot of room for contributed patches :)
Famous last Words
Why do I use OpenBSD?
Secure and sensible defaults, -current, no surprises, dozens of exploit mitigations, all-in-one solution, excellent documentation, active community.
Reasons not to use OpenBSD
Commercial OTS software, 21st century file system, high performance, NUMA architecture or you simply don't like it.
| Q & A |
Thanks for listening!
xhr@giessen.ccc.de |